
IT/OT convergence will generate $1.2 trillion by 2023.
Artificial Intelligence of Things (AIoT) Market is forecasted to grow by $124.9 Billion by 2033, with a CAGR of 37.7%.
Source:
https://finance.yahoo.com/news/aiot-platforms-market-grow-cagr-180000157.html
3 new laws with fines and penalties governing IoT in critical infrastructure came into effect since 01/01/24.
Many more coming.
Involvement of CISOs in OT cybersecurity decision making increased from 88% in 2022 to 95% in 2024.
70% of industrial organizations fell victim to cyberattacks in 2023 and 26% faced attacks weekly or more.
Source:
https://www.paloaltonetworks.com/blog/network-security/state-of-ot-security-2024/
In 2023, there were twice as many software supply chain attacks as in the previous three years combined, costing businesses $46 billion* to address 245,000 supply chain incidents.
Source: https://www.juniperresearch.com/press/study-reveals-staggering-cost-of-software-supply
Source:
https://www.sonatype.com/state-of-the-software-supply-chain/open-source-supply-and-demand
14 billion industrial automation devices will be connected to the internet by 2027. That's about 20 percent of all IoT devices.
Lynda Stadtmueller, research vice president and global practice area leader at Frost & Sullivan

If all of the hype were true, there would not be an IoT/OT SecOps crisis in 2024. Need to separate fact from fiction in the IoT/OT device operations market.

Case study with market leaders in the IoT/OT device management market space.
Company
names have been obfuscated to protect the not-so-innocent.


"Find, fix, and manage every IoT, OT, and IoMT device"
Word choice of ‘every’ would be fine in marketing parlance if it were remotely accurate.
"The industry's most advanced ICS/OT cybersecurity software"
High reliance on manual processes and network mitigation is not 'industry's most advanced'
"One platform to manage and secure your [IoT] software supply chain"
Many, many caveats making the 'one platform' & secure 'software supply chain' claims a bit dubious
Closing the gaps with guiding principles

all devices, protocols, software

automate & simplify

deep / wide visibility > blind spots
Intelligent Digital Twin is the path forward for complex operational environments, especially in modern IoT:


Introducing the ByteTrail ecosystem - solving the IoT / OT perfect storm with modern software to a rapidly evolving threat and compliance landscape.
Simply bring your own:



By closing the gaps found in conventional solutions.
The Operational Software Supply Chain maintains a detailed 'list of ingredients' of software, dependencies, configurations, and more.
360° Device Visibility
“List of Ingredients”
Software Bill of Materials
Operations Bill of Materials








A significant challenge in IoT / OT is the wide variety of external and internal sources required to
build and
maintain comprehensive domain knowledge, particularly when supporting critical
infrastructure.
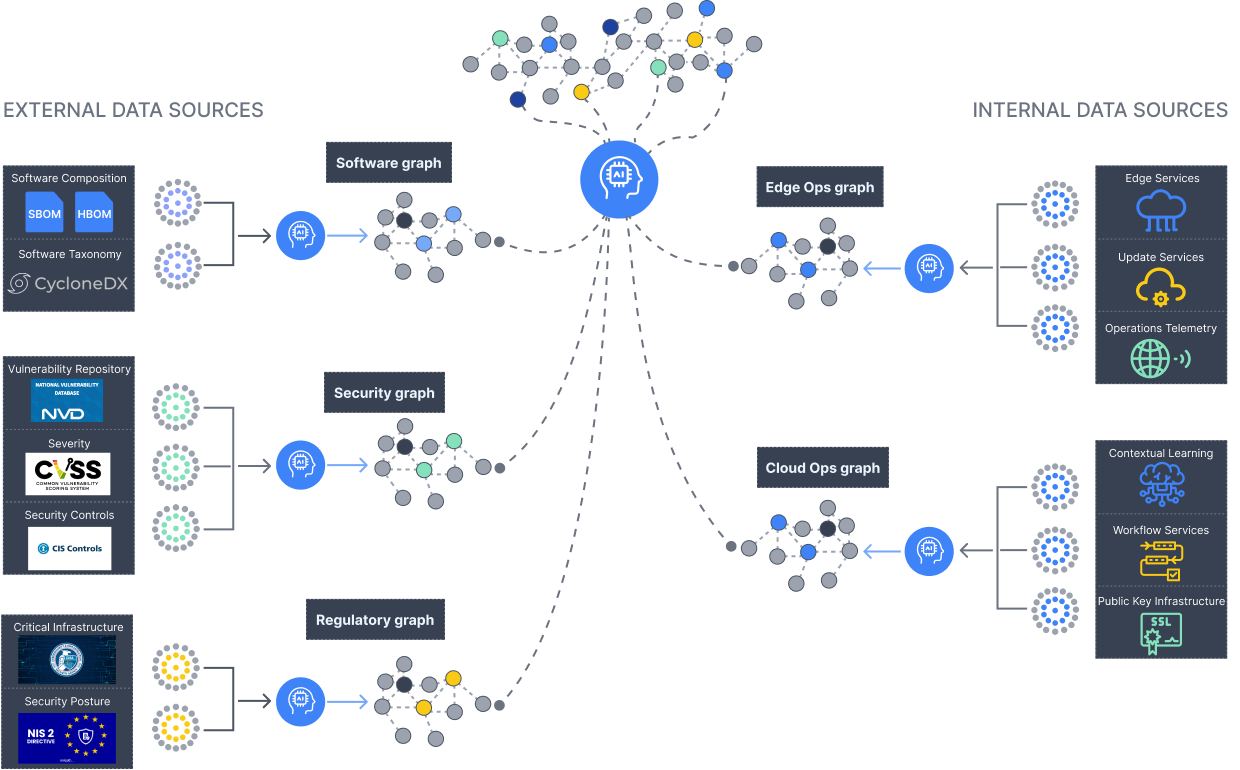
ByteTrail combines the Digital Twin of the physical and digital worlds, with intelligence derived from unlocking hidden operational knowledge while providing human-AI interaction powered by GenAI. The result is a Secops revolution in IoT/OT, otherwise known as the Intelligent Digital Twin.
-automation-



-automation-











The Intelligent Digital Twin with human-AI interaction results in high levels of determinism - meaning the results, responses, and actions are accurate and always contextually relevant. All done in all near-real time.
